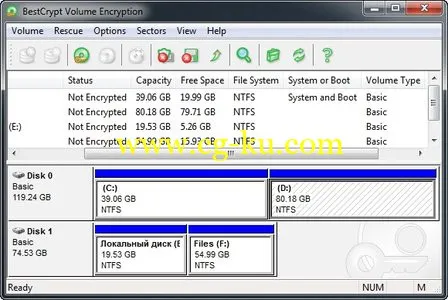
estCryt是一款创建并支持加密的虚拟分区的软件。虚拟分区以“container”的形式存在,备份和移动都不影响BestCryt对其读取和更改。BestCryt能在Windows环境下运行,并发挥这些操作系统的最大性能。BestCryt可以通过网络远程在多种操作系统的环境下创建“container”文件。为了保证安全性,加密的虚拟分区可以以超时或者快捷键的方式关闭。删除任何“container”文件需要用户通过密码认证并确定。这是它的大客户采购版。
结合秘密金匙密码系统与公开金匙密码系统,为俱有双重功能及优点的混合型密码系统(Hybrid Cryptosystem),使您的文件得到最完整的保护,轻易达成文件传输的保密性(非法窥视)、完整性(非法拦截并窜改)、辨识性(有对方之数位签章);及不可否认性(有对方之数位签章)。
BestCrypt Volume Encryption 3.50.20 Multilingual | 6.3 MB
Jetico's BestCrypt Volume Encryption software is an evolved class of disk encryption products that allows users to encrypt old MS-DOS style disk partitions, modern volumes residing on a number of physical disk devices - for example Spanned, Striped, Mirrored or RAID-5 volumes - and Windows 8 Storage Spaces.
New features in version 3
BestCrypt Volume Encryption version 3 provides the next evolution in performance and security from the pioneers in native encryption for disk volumes.
1. More robust support of encrypted disk volumes. To reconfigure the size, location or type of software RAID, earlier versions of the software first required decryption of the encrypted volumes. Now version 3 of BestCrypt Volume Encryption automatically adapts its internal information for encrypted volumes when changing their configuration. (Read Update Notes)
2. Two-Factor Authentication with conventional removable disks (like USB sticks). With version 3 of BestCrypt Volume Encryption, encryption keys can be moved to removable storage.So anyone who wants to access an encrypted volume must: 1) know password for the key; 2) have the removable disk where the key is stored. (Read Update Notes)
3. Added layer of security by booting of encrypted volumes from trusted network. In this case, encryption keys of boot/system disk volumes are not stored on the local computer, but on a network server. Enterprises can now benefit from an additional level of security. Since encryption keys are stored on an enterprise server, access to encrypted computers will be only possible when connected to the enterprise network. (Read Update Notes)
4. Speed boost from support for new machine instructions (AES-NI) in the latest Intel processors. As a result, speed of the AES encryption module utilizing AES-NI instructions increased up to 5 times. Disk access to the encrypted volumes now operate up to 30% faster.
5. Faster initial encryption. Earlier versions of the software encrypted a whole disk volume sector-by-sector, including unused disk space. If disk is large (terabytes), initial encryption process requires dozens of hours. In version 3 of BestCrypt Volume Encryption, if the volume is empty, the user can run Format and encrypt process that will avoid long sector-by-sector encryption. The volume will be just marked as 'encrypted' and all the data written to the volume later will be encrypted. Unused disk space remains unencrypted. Optionally, the user can run Erase, format and encrypt process. In that case, the volume will be wiped (overwritten), formatted and marked for encryption.
6. Secure unattended reboot. Version 3 of BestCrypt Volume Encryption utilizes Trusted Platform Module (TPM) hardware available on many motherboards for the purpose of unattended reboot of computers with encrypted boot/system disk volumes. This feature is necessary to manage servers that are required to function around the clock. If such a server has an encrypted boot/system volume, every reboot of the server requires manual password entry at boot time. With this new feature, a server administrator can choose an interval of time when BestCrypt Volume Encryption (with help of TPM) should support unattended reboot of the server. (Read Update Notes)
7. Support of eToken Pro Java hardware from SafeNet (former Aladdin). Earlier versions of BestCrypt Volume Encryption supported Two-Factor Authentication with the help of eToken R2 and eToken Pro hardware. eToken Pro Java is the latest hardware designed by SafeNet for such a purpose.
8. Added convenience for mounting volumes and protection against accidental formatting. When Windows discovers that an encrypted unmounted volume has been connected, it asks for the volume to be formatted. In some cases, this resulted in accidental formatting of encrypted volumes. Version 3 of BestCrypt Volume Encryption now has the option to disable Windows formatting messages and offers an additional option to suggest mounting the volume for access.
9. Added support for other physical sector sizes. Disk devices with physical sector sizes other than 512 bytes are now supported in version 3 of BestCrypt Volume Encryption.
OS :
Windows XP, Vista, 7, 8 (32-bit / 64-bit)
Language
: Multilingual
Home Page
-
http://www.jetico.com/
Download freakshare
http://freakshare.com/files/86x1sa7y/BestCrypt.Volume.Encryption.3.50.20.rar.html
Download filefactory
http://www.filefactory.com/file/6n99e8vldyzd/BestCrypt.Volume.Encryption.3.50.20.rar
发布日期: 2013-06-24