IT Surveillance and Computer Forensics from Scratch (Update)
MP4 | AVC 517kbps | English | 1152x720 | 24fps | 8h 30mins | AAC stereo 40kbps | 1.3 GB
Genre: Video Training
Surveillance Methods and Computer Forensics Basics - 101 Video Training with PDFs. Before we begin: the practical use of the course you are going to see has been proven by thousands of people all over the world – beginners and computer geeks as well. People who make their first steps in computer / network security and professionals: network administrators, programmers, pentesters, black- and white hat hackers. Please, read carefully what we'd like to share with you.
What you can expect from this course and what you will learn:
You will get over 37 lectures and 8.5+ hours of content!
You will get free source code package to download
You will learn: Transmitting volatile evidence from an evaluated system
Disk backup over the network
Searching data based on last access or modification timestamps
Analyzing the data sent by a web browser
Analyzing the data revealed in e-mail headers
Remote capturing the data about user and hardware
Harvesting user's IP address on message board
Methods of creating a partition image
Hiding data inside NTFS alternate data streams
Steganography techniques
Using tunneling to access firewall-protected services
File encryption methods and vulnerabilities
Recovering MS Windows user passwords
Analyzing run applications based on Prefetch folder
Acquiring data from pagefile, thumbnails and raw disk fragments
Acquiring data from binary files and process memory dump
Acquiring data from e-mail files
Acquiring user's browsing history
Discovering web search queries
Examining remote host's availability over LAN
Checking e-mail's deliverability and analyzing recipient's data
Creating and installing a keylogger
Building custom tools to analyze system security
Taking over a remote computer
Restricting access to chosen websites and computers
Using WMI console for acquiring and analyzing evidence
Using DNS cache for gathering information on visited websites
Using Sleuth Kit for acquiring data from a disk image
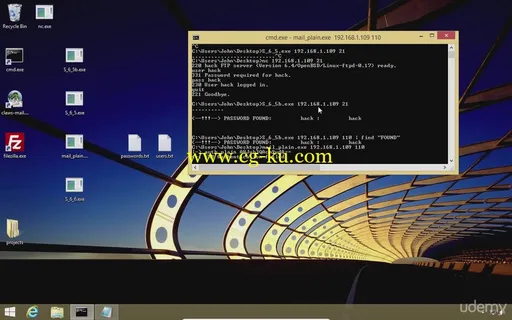
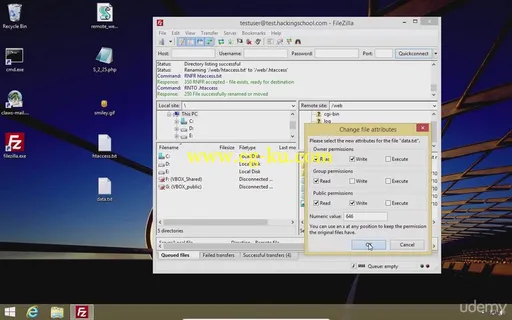
Recovering passwords to FTP, e-mail accounts and websites
Analyzing a corporate data leak scenario
We guarantee your 100% satisfaction or you will get your money back. You have 30 days to decide if the Wireless Network Hacking Course is for you. You will get access to the whole system. If for any reason you're not satisfied with your training, you will get a full refund. No questions asked.
Good luck and see you on the other side,
Andrew Harper || Hacking School Team

发布日期: 2016-02-13